Transport Layer Security (TLS) are cryptographic protocols designed to provide communications security over a computer network, typically between a website and a browser.
- Enable Tls 1.2 On Chrome For Macsportfasr Pc
- Enable Tls 1.2 On Chrome For Macsportfasr Mac
- Enable Tls 1.2 On Chrome For Macsportfasr Windows 10
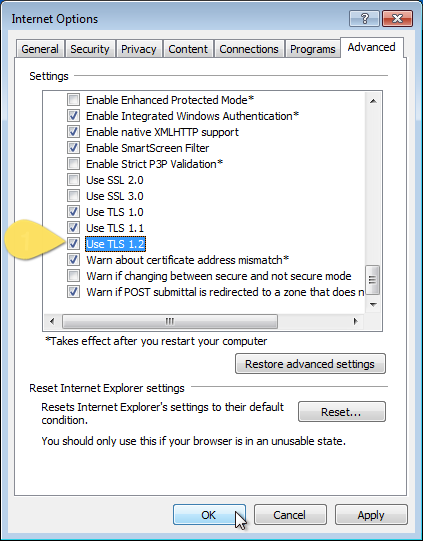
TLS 1.0 and its deprecated predecessor, SSL are vulnerable to some well-known security issues such as POODLE and BEAST attacks. According to NIST, these vulnerabilities cannot be fixed or patched, therefore all companies, especially banks and other financial institutions who are notoriously slow in upgrading theirs systems, need to upgrade to a secure alternative as soon as possible, and disable any fallback to both SSL and the older TLS 1.0.
Enable Tls 1.2 On Chrome For Macsportfasr Pc
Starting with Google Chrome 79, Chrome will give sites a 'not secure' label if TLS 1.0 or TLS 1.1 is used. The main intention is to provide users and webmasters with information that they may act upon; webmasters need to enable TLS 1.2 or later on the server to address the issue. Check out my previous article about how to enable TLs 1.3 in Apache, Nginx and Cloudflare. But how about client-side – browsers? Chrome starting from 63 version and Firefox 61 have started supporting TLS 1.3, and if your browser doesn’t support this yet, then you are missing the performance and privacy features. Enabling TLS 1.3 in Chrome.
As of 30 June 2018, SSL and TLS 1.0 should be disabled and more secure encryption protocol such as TLS 1.2 (or at the minimum TLS 1.1) is required to meet the PCI Data Security Standard (PCI DSS) for safeguarding payment data.
The next question then how on do we enable TLS 1.2 on Windows Servers? Especially on older servers such as Windows Server 2008 as many companies are not on the latest and greatest operating systems?
This post will address what to look for and how to enable TLS 1.2 as the default protocol for Windows Server 2012 R2 or older.
IMPORTANT: As always and it’s worth repeating, you need to backup your current registry settings before attempting any of these changes on your servers.
Enable TLS 1.2 on Windows Servers 2008 SP2 or later
The blanket statement to enable your TLS 1.2 on your server from Windows Server 2008 SP2 or later. Microsoft provided an update to add support for TLS 1.1 and TLS 1.2 for Windows Server 2008, but it requires Windows Server 2008 SP2 installed.
So just to state the obvious, TLS 1.1 and TLS 1.2 are not supported for 32-bit Windows Server 2008 SP1.
Launch regedit.exe.
In registry, go to:
Create a new DWORD entry with a name TLS 1.2 and create another subkey Client and Server.
Under the subkey Server, create another DWORD Enabled with a value of 1.
Still under the subkey Server, create a DWORD DisabledByDefault with a value of 0.
You must create a subkey DisabledByDefault entry in the appropriate subkey (Client, Server) and set the DWORD value to 0 since this entry is set to 1 by default.
Reboot the server and test.
Enable TLS 1.2 on .NET Framework 3.5 (including 2.0)
.NET Framework 3.5 or earlier did not originally provide support of applications to use TLS System Default Versions as a cryptographic protocol. However, for Windows Server 2012 R2, check if KB3154520 is installed (or KB3154519 for Windows Server 2012; KB3154518 for Windows Server 2008 R2; KB3154517 for Windows Server 2008 SP2).
How to check the KB updates
Right-click on the Windows button and select Programs and Features.
On Programs and Features window, click onthe View installed updates on the left pane.
You will see a list of the updates that you can narrow down or do a very specific search by using the Search Installed Updates box. You can type in the KB number (i.e., “KB3154520”).
If the corresponding KB is already installed, we just need to enable it via registry change. Otherwise, you need to install the patch from either of the links for Windows Server 2012 R2 (or use the same corresponding links above for earlier versions of Windows Server).
Registry Change
Launch regedit.exe.
Go to:
Create a new entry SystemDefaultTlsVersions with a DWORD value set to 1.
Create a new entry SchUseStrongCrypto with a DWORD value set to 1.
Go to:
Create a new entry SystemDefaultTlsVersions with a DWORD value set to 1.
Create a new entry SchUseStrongCrypto with a DWORD value set to 1.
For 64-bit OS, the same changes also needed for the following locations:
Create a new entry SystemDefaultTlsVersions with a DWORD value set to 1.
Create a new entry SchUseStrongCrypto with a DWORD value set to 1.
Go to:
Create a new entry SystemDefaultTlsVersions with a DWORD value set to 1.
Create a new entry SchUseStrongCrypto with a DWORD value set to 1.
Test.
Enable TLS 1.2 as default for WinHTTP
This may be applicable for any Classic ASP or VB6 applications that use WinHTTP. Prior to Windows 10 and Windows Server 2016, TLS 1.1 or 1.2 is not enabled by default for client-server communications through WinHTTP.
To set TLS 1.2 by default, do the following:
Create a registry entry DefaultSecureProtocols on the following location:
Set the DWORD value to 800 for TLS 1.2.
For 64-bit OS, repeat step 1 and 2 on the following location:
Reboot the server and test.
Windows 10 and Windows Server 2016 support TLS 1.2 for client-server communications by using WinHTTP.
Further Reading
Update to enable TLS 1.1 and TLS 1.2 as default secure protocols in WinHTTP in Windows
TLS/SSL Settings
How to enable TLS 1.2 for Configuration Manager
Transport Layer Security (TLS) best practices with the .NET Framework
Support for TLS System Default Versions included in the .NET Framework 2.0 SP2 on Windows Vista SP2 and Server 2008 SP2
Support for TLS System Default Versions included in the .NET Framework 3.5.1 on Windows 7 SP1 and Server 2008 R2 SP1
Support for TLS System Default Versions included in the .NET Framework 3.5 on Windows Server 2012
Support for TLS System Default Versions included in the .NET Framework 3.5 on Windows 8.1 and Windows Server 2012 R2
Enable Tls 1.2 On Chrome For Macsportfasr Mac
Download
Solving the TLS 1.0 Problem (MS Word document)
Overview
| Finding ID | Version | Rule ID | IA Controls | Severity |
|---|---|---|---|---|
| V-81583 | DTBC-0056 | SV-96297r1_rule | Medium |
| Description |
|---|
| If this policy is not configured then Google Chrome uses a default minimum version, which is TLS 1.0. Otherwise, it may be set to one of the following values: 'tls1', 'tls1.1' or 'tls1.2'.When set, Google Chrome will not use SSL/TLS versions less than the specified version. An unrecognized value will be ignored.'tls1' = TLS 1.0'tls1.1' = TLS 1.1'tls1.2' = TLS 1.2 |
| STIG | Date |
|---|---|
| Google Chrome Current Windows STIG | 2018-09-06 |
Details

Enable Tls 1.2 On Chrome For Macsportfasr Windows 10
| Check Text ( C-81333r1_chk ) |
|---|
| Universal method: 1. In the omnibox (address bar) type chrome://policy 2. If 'SSLVersionMin' is not displayed under the 'Policy Name' column or it is not set to 'tls1.1', this is a finding. Windows method: 1. Start regedit 2. Navigate to HKLMSoftwarePoliciesGoogleChrome 3. If the 'SSLVersionMin' value name does not exist or its value data is not set to 'tls1.1', this is a finding. |
| Fix Text (F-88409r1_fix) |
|---|
| Windows group policy: 1. Open the “group policy editor” tool with gpedit.msc. 2. Navigate to Policy Path: Computer ConfigurationAdministrative TemplatesGoogleGoogle ChromeContent Settings Policy Name: Minimum SSL version enabled Policy State: Enabled Policy Value: TLS 1.1 |
